Advancing the state of offensive security
Industrialize offensive security with AI tools used by the best red teams, researchers, and model builders in the world.
Our Collaborators
Our solutions are built in close collaboration with government agencies, safety institutes, enterprises, and frontier model companies. We're currently supporting our partners with custom agent and capability development, cyber evaluations, synthetic data generation, and beyond.
Government
Enterprise
AI Labs
Bringing scale to offensive security
Augment your security team with Strikes and our comprehensive agent library. Deploy our pre-built agents into your environment—or build, evaluate, and improve your own.
We’re dialed in on building agents for the offensive security domain. Our ready-to-use agents range from vulnerability discovery and exploitation to network ops and threat intel.
Transform your proof-of-concept into a working agent that can deploy real-world attacks at scale.
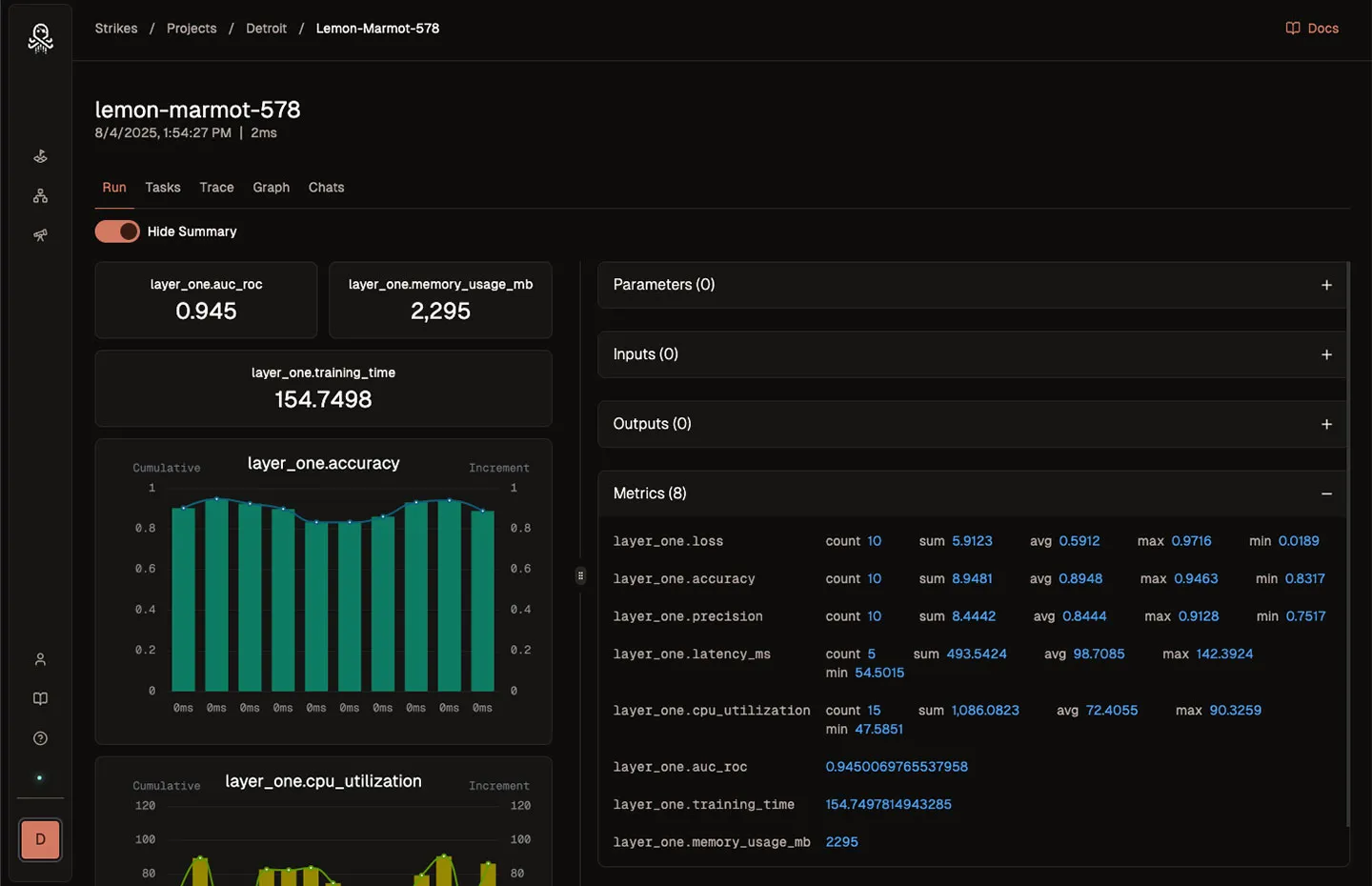
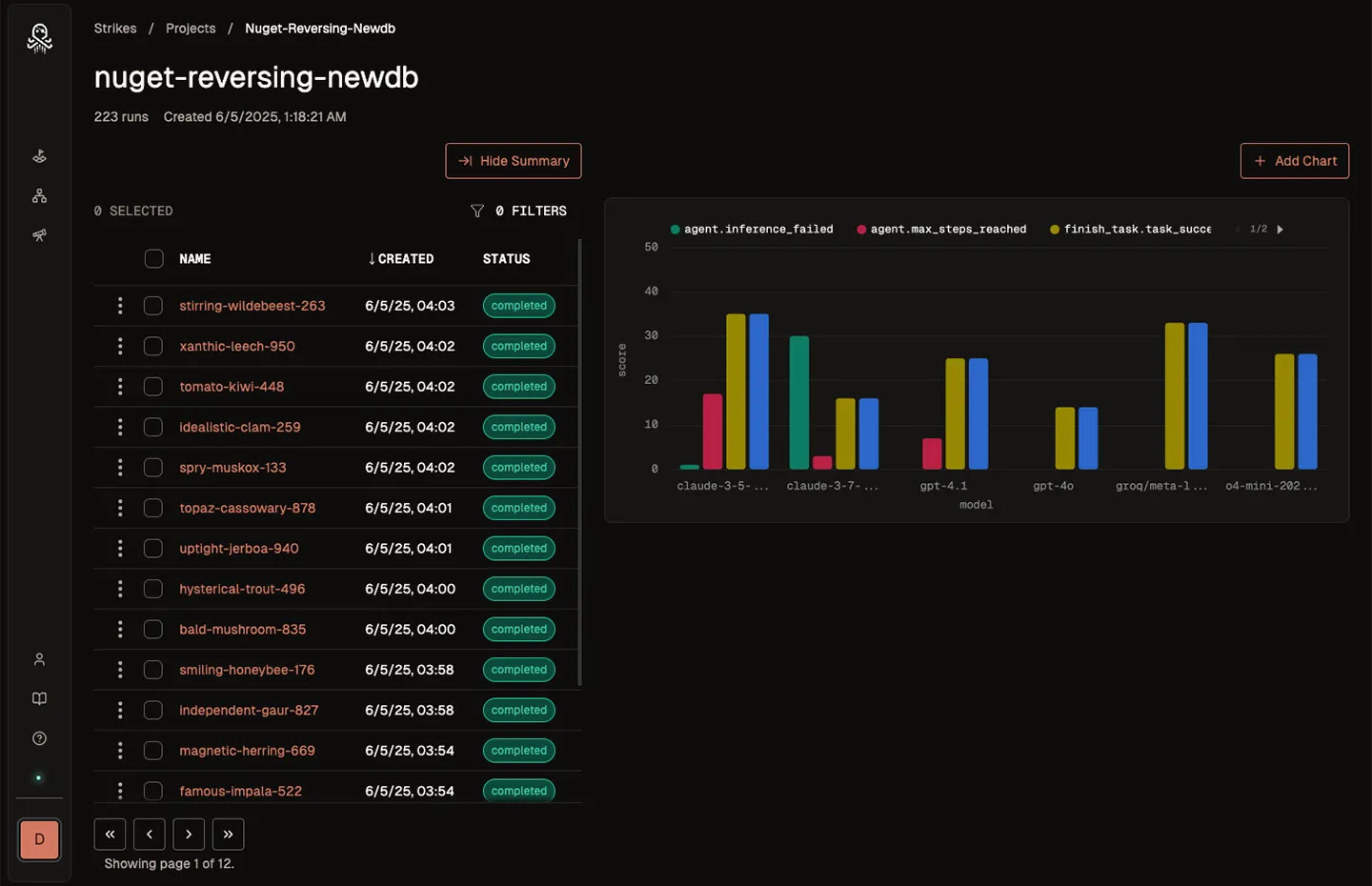
Gain confidence that you have the best performing agent architecture. Make development decisions based on eval metrics, not vibes.
Evaluate deployed AI systems
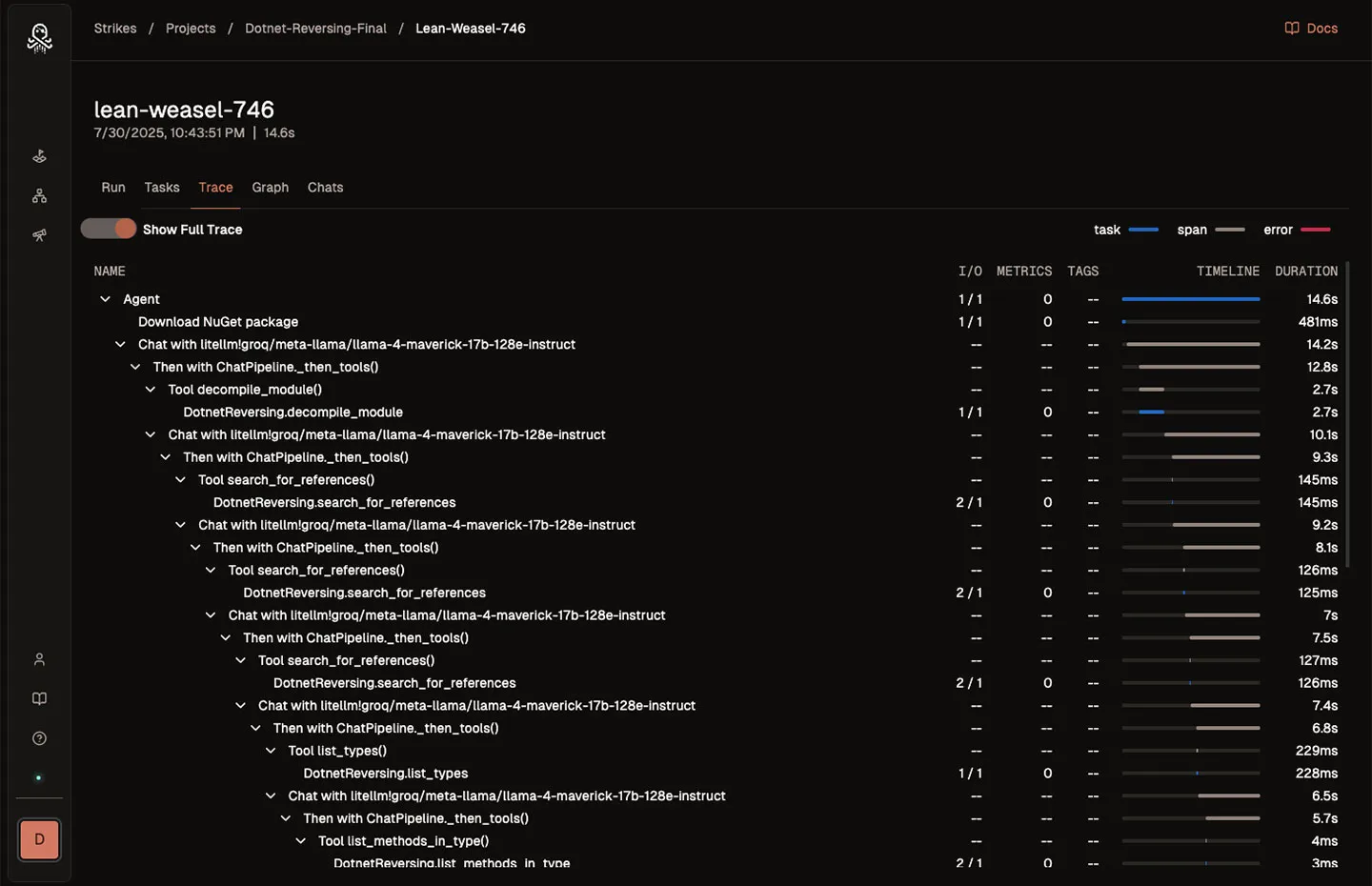
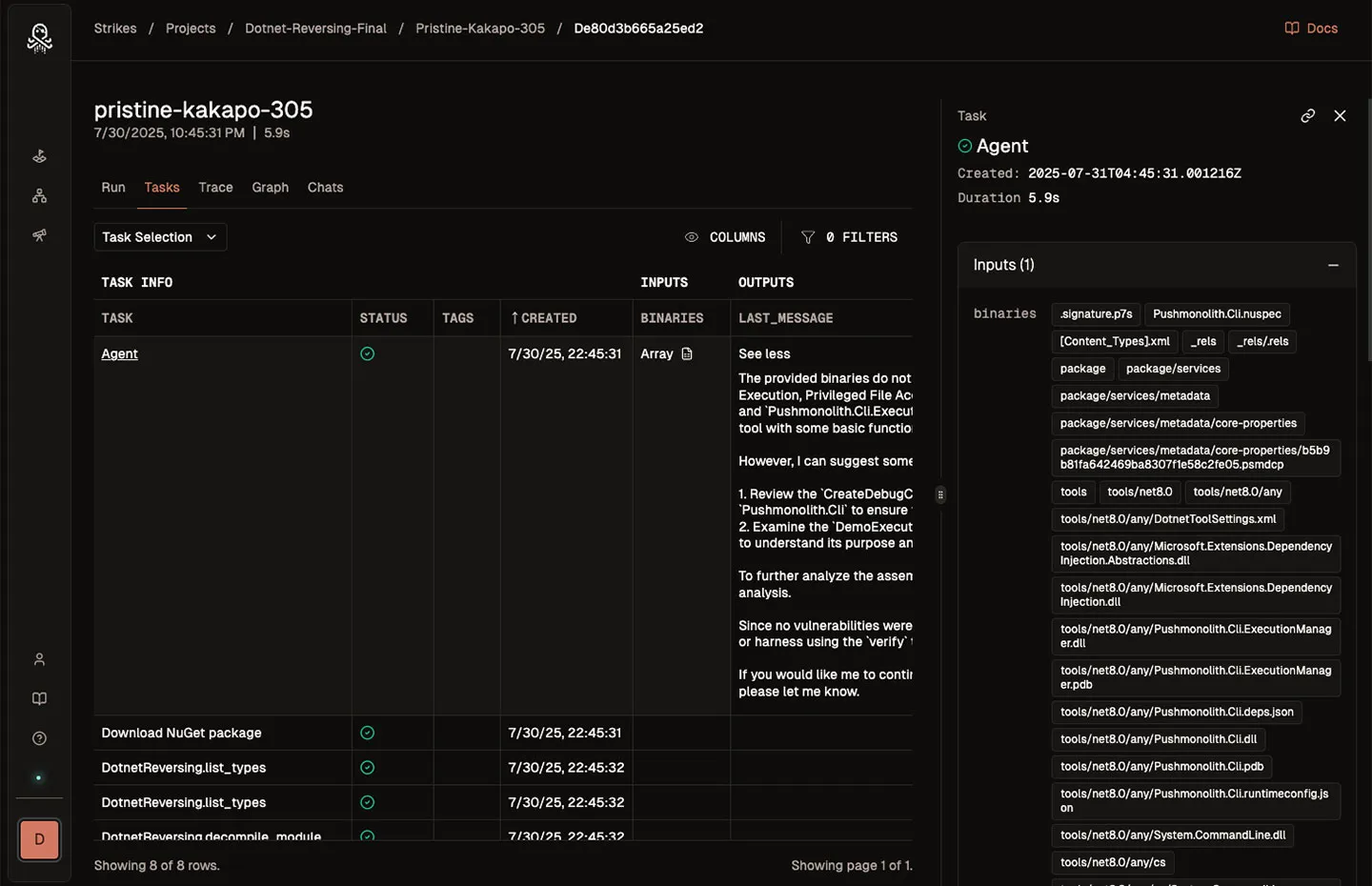
Perform adversarial research and execute operations in Strikes. Categorize, assess, and mitigate enumerated risks presented by AI deployments.
Integrate the latest adversarial research or perform your own using our SDK.
Test any model. The vast majority of deployed models are not LLMs.
Strikes supports multiple users, centralized storage, and scoped reporting.
Learn to hack and evaluate AI systems
Advance your AI hacking domain knowledge alongside thousands of offensive security practitioners.
Catch up on the latest models and techniques.
Learn how to attack different types of models and deployments.
Enterprise users can deploy their own models into a evaluation environment.